ATTENTION! Your PC is blocked due at least one of the reasons specified below.

The warning is dire. You’ve been “caught” doing something illegal. Your photos and other data have been locked away from you because it’s “evidence” against you. But don’t worry, if you pay the “fine,” all will be released and you’re off the hook.
Don’t pay and, well, say farewell to your photos.
The grammar is a tip off to a scam, but the threat is very real.
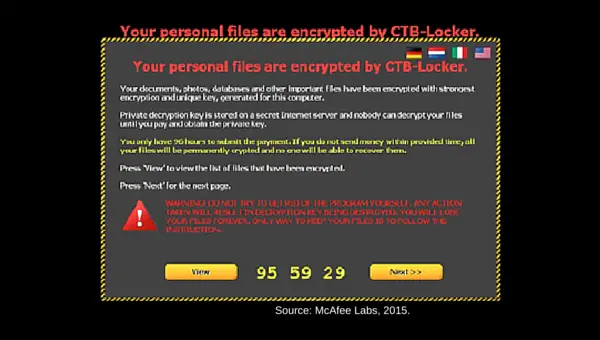
Your Photos Held Hostage
You’ve become a victim of ransomware. Ransomware is a type of malware that restricts your access to your files by encrypting them. The attack holds the data hostage and contacts you demanding money in exchange for a decryption key to unlock your files.
Older versions were easily by-passed by the user. Newer, advanced versions use up to date encryption technology and the latest strains can jump to networked drives and cloud storage.
Unfortunately, being cheap to use makes these online break-in and stickup scares more common and easier to execute. According to Intel Security, there has been a 165% increase in attacks since the first quarter of 2015.
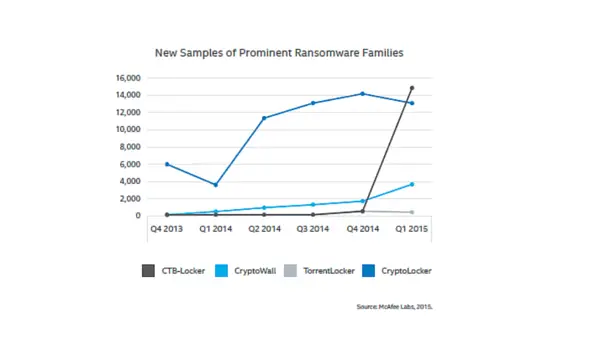
A few other bad things. Usually the money demand is in Bitcoin which makes it difficult to trace. Because Bitcoin is still new, it’s difficult for some people to get set up in time to make the payment. But, don’t worry, the criminals are starting to give you instructions.
Many authorities say don’t pay and call the police. But if you don’t pay, your data stays encrypted. It’s usually in a form that’s difficult to crack, if at all. Software removal won’t necessarily work. Some variants can detect if the main program has been deleted and, rubbing salt into the wound, demand that you re-install it. Yes, it even gives you a link. If you do pay, you get the key to unlock your software.
Or not if your particular criminal is feeling cantankerous.
How about avoiding the issue all together?
Unsafe Websites, Email Phish and Attachments
Ransomware comes from the usual culprits: rogue websites, phishing scams, trick attachments and bad software. All the things we’ve come to expect from viruses, Trojans, and malware. But the latest versions can also compromise genuine advertising causing another path to infection.
And because technology evolves so rapidly, it’s almost impossible for law enforcement and security professionals to keep up.
The Solution: Safer Surfing, Better Email Management and Backups
So how do you avoid ransomware? By using the same techniques to avoid viruses and malware:
- Safer Surfing by recognizing bogus websites.
- Better email management. Pay close attention to unsolicited links and attachments in your email.
- Keep the operating system and the software up-to-date.
- Keep your antivirus and malware software up-to-date.
- Create and maintain a scheduled backup of important files and system images. Then, most important, keep the backups stored off-line and off site.
What to Look Out For
First, learn how to recognize a bogus website.
- Check the URL to verify it’s going to a legitimate site. A link like www.paypal.com is good; paypal.someothername.com is bad.
- Look for spelling and grammar mistakes – taking into account the country the real site is in. For example, UK English versus US English.
- Watch for deals that are too good to be true. They generally are unless it’s old stuff a legitimate site is getting rid of. A phone call can determine that.
- Be on the lookout for suspicious downloads. If you need to download it, scan it before opening.
Second, pay closer attention to your email.
- Is the email from somebody you know or expecting to hear from?
- Is the attachment something you’re expecting?
- Are there links in the email that you’re expecting?
- If the answer is no to any of those questions, delete the email.
- Turn off the feature that opens a preview of the email. A preview is as good, or bad, as a click.
- Set up your spam filter.
How to Survive the Stick up
To protect yourself in case the worst happens, set up and put into practice a good disaster recovery backup/archive program. This is what comes to the rescue if you get hit by ransomware.
Here’s a simple plan that involves two external hard drives. Simple means a better chance it will get done and be maintained. If you’re really paranoid, buy a third drive. They really are out to get you.
Using two or more drives will allow you to keep one on site for a fast local restore and another off-site in case of a disaster, like a fire, at the office or home.
Backup What Exactly?
First, take some time to get an idea of what you want to protect. At the least, backup any data that you can’t or would be hard-pressed to re-create. Things like:
- Your business data.
- Your photographs.
- Any customer related data — albums, photographs, email, contracts.
- Your software preferences — It’s also a good idea to have backup copies of your software and keep them stored with your data backups.
- Your email and any other business communications.
- Any photographs or data that you post to social media sites — to protect against the site disappearing or suffering an outage and losing your data.
- Any personal data that you would need in a disaster.
Now it’s time for a trip to the local big box store or Amazon. Buy two or more large capacity external hard drives – 2TB+ – that are USB 3.0/eSATA/FireWire/Thunderbolt capable. If you use a Mac make sure the drives are formatted for the Mac.

Back it Up
Apple and Microsoft offer their own back up routines which are relatively easy to set up though somewhat limited.
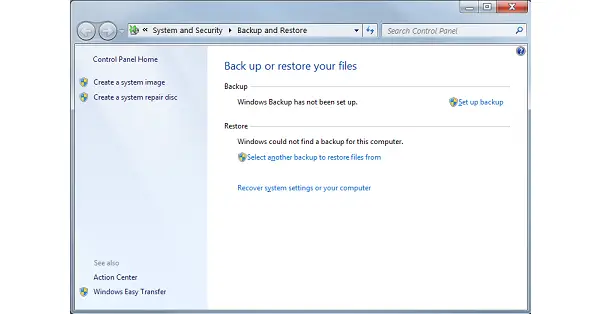
Microsoft’s Backup utility can make a system image to help in restoring your PC. The system image allows you to bypass having to reinstall the OS and software. A drawback is that it sometimes fails when trying to restore to a new hard drive or SSD.
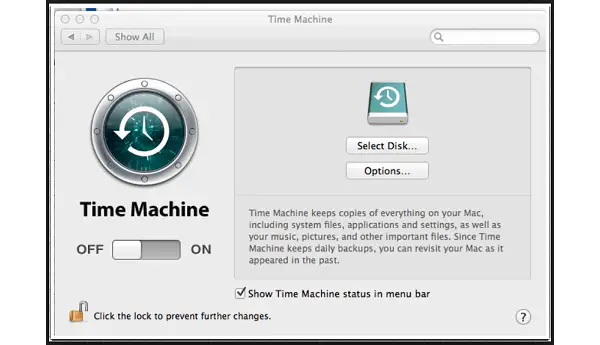
Apple’s Time Machine drawback is the deletion of the oldest backups when you get within reach of the external drive’s capacity. You do get a warning first.
The external drives you purchased probably came with backup software and will automate the process but don’t allow much control.
My recommendation is dedicated third party software that combines backup, archive and system image capability. You can then accomplish these three tasks easily with greater flexibility and control.
You can find packages below $100 and it’s well worth it for the peace of mind and safety of your photos.
At the most basic, here are the steps to set up your backup:
- Hook up the first external drive.
- Fire up the backup program.
- Choose the external drive as the destination for the backup.
- Select all of the available partitions for the first backup.
- Kick the backup off.
- Repeat the process for the second drive.
If you bought third party software:
Create a system image and recovery disks.
When done, disconnect the drives and store them. One should remain onsite for immediate recovery, and the other(s) should go offsite. A safe deposit box is reliable storage.
The important thing to remember is that the external drives are to be connected to the computer only when you’re backing up or restoring. Any other time, they are offline to prevent malware from getting to that data.
With these steps your data is backed up and stored safely. If the worst should happen, you can quickly get back to business.
Whether through a manual re-install or using a system image, your backups will solve your photo hostage crisis.
So, what are you waiting for? Get going on those backups and let me know how it goes in the comments.









0 comments